…R. Shmeleva, W. Retschitzegger, B. Pröll Security of grid structures under disguised traffic attacks, Cluster Computing, 19(3) 2016, 1183–1200. Online 17 June 2016. DOI:10.1007/s10586-016-0582-9 The zipped folder containing the model…
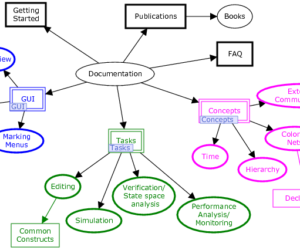
Publications
…Press, Cambridge, 2010. There are also online references for Standard ML: Programming in Standard ML by Robert Harper The Standard ML Basis Library (excellent manual) Standard ML of New Jersey…
Temporal logic for state spaces
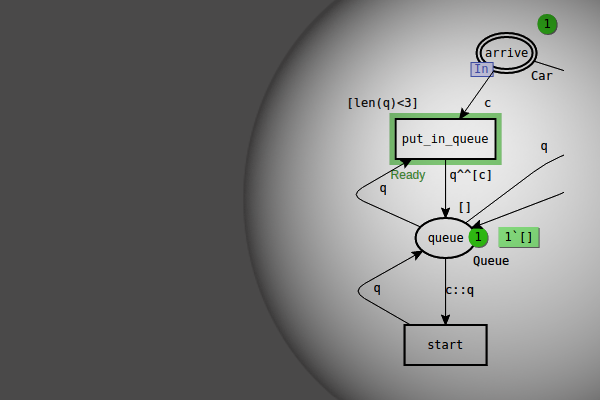
…net This net can be found in a subdir of cpntools called Samples\\DiningPhilosophers. Additional information Additional information about the facilities is available online: Technical report Slide presentation Related pages Verification…
Help entry in index
…back to the main help page. Link to main help page Overview of Help pages There are a number of categories of help pages including: Add/edit declarations Add/edit inscriptions Adding…
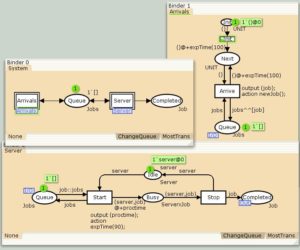
Queue system example
…job that is removed from the head of the queue. Processing times for jobs are exponentially distributed with a mean processing time of 90 time units. The Stop transition will…
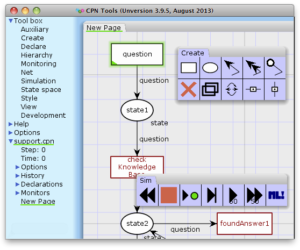
Is there a user manual for CPN Tools?
…want and add them to your book. When you are done, click Show, modify book, and follow the guide-lines to download your manual as a PDF. Note that some formatting…