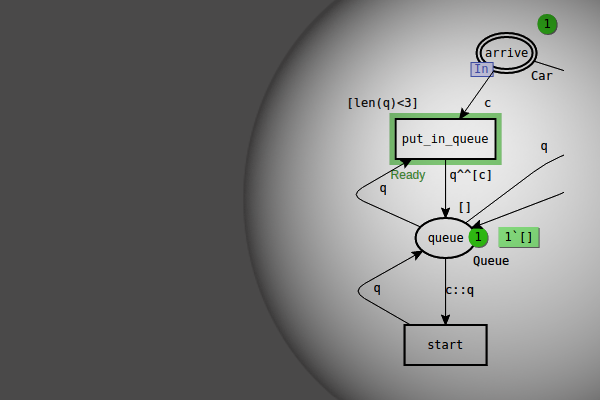
The model consists of an 8×8 matrix of switching nodes that deliver packets to computing nodes which are attached to the matrix borders and produce and consume packets. Traffic guns are added to the model to represent traffic attacks. Simulation in CPN Tools revealed simple and dangerous traffic gun configurations.
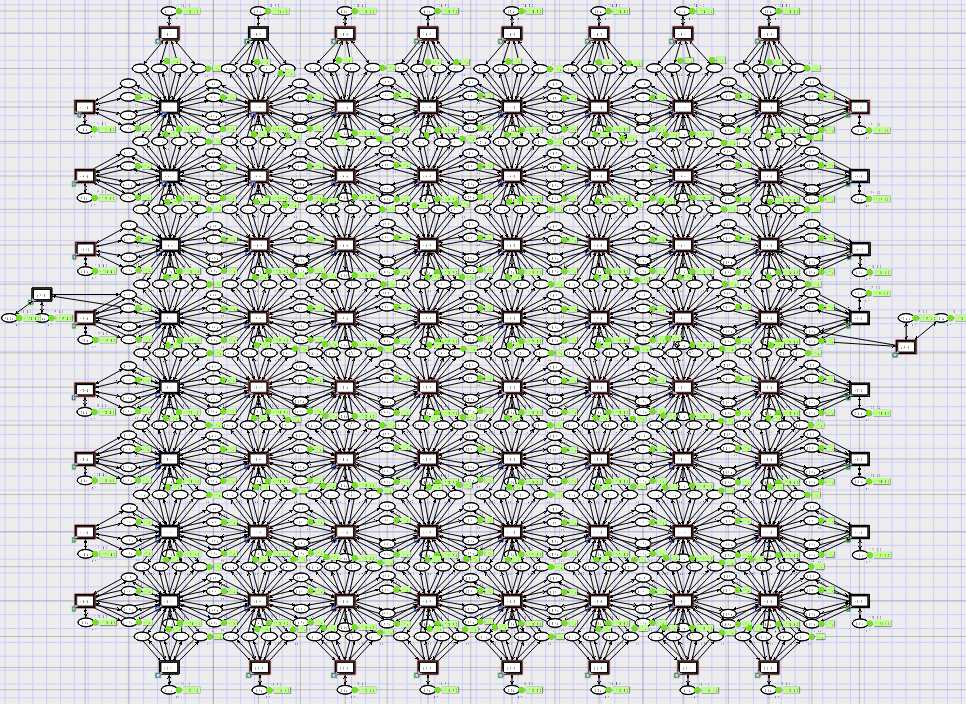
Screenshot of the 8×8 matrix
D. A. Zaitsev , T. R. Shmeleva, W. Retschitzegger, B. Pröll Security of grid structures under disguised traffic attacks,
Cluster Computing, 19(3) 2016, 1183–1200. Online 17 June 2016. DOI:10.1007/s10586-016-0582-9
The zipped folder containing the model (grid8x8.cpn) (Note that loading this model may take several minutes, please be patient).