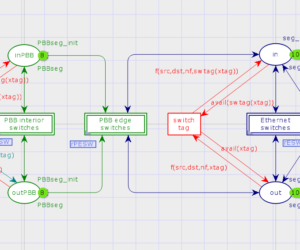
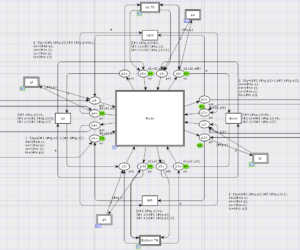
The model has the same structure for any given PBB network. It evaluates the maximal and average network response time on-fly. The network topology is inputted as a value of dedicated constant together with other parameters such as addresses of various types of terminal and communication equipment their performance and the number of ports. Reenterable models are devised for model-driven design of networks. Dmitry A. […]
Reenterable Model of Rectangular Communication Grid with Cut-through Nodes
A reenterable model of communication grid with cut-through nodes is constructed. The cut-through transmission of packets works fast, because it uses only the head of packet, which contains the destination address, for the forwarding decision. The reenterable models of the grid structures do not depend on the grid size that is the main advantage of reenterable models. The grid performance and average packet delivery time […]
Reenterable Model of Rectangular Communication Grid
A reenterable model of communication grid with store-and-forward (SAF) nodes is constructed. The reenterable models of the grid structures do not depend on the grid size that is the main advantage of reenterable models. The grid performance and average packet delivery time are evaluated for various intensity of Poisson and Uniform distributions. Shmeleva T.R. Efficiency estimation of computing grids with various traffic types. Proceedings […]
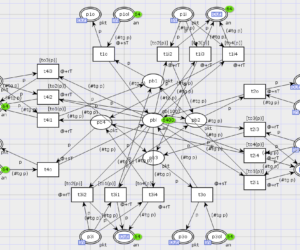
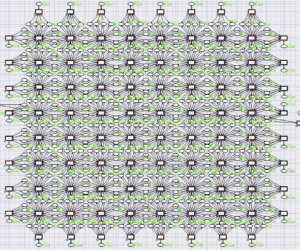
Rectangular Grid with Cut-through Switching Nodes
The model is composed of packet switching nodes situated on a rectangular grid and generators of traffic attached to the grid borders. It is supplied with malefactor models in the form of traffic guns disguised under regular multimedia traffic. Switching nodes use cut-through transmission of packets that works fast, because it uses only the head of packet, which contains the destination address, for the forwarding […]
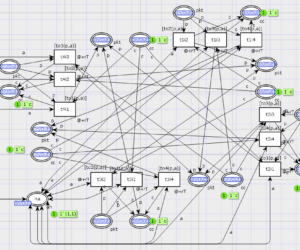
Rectangular grid under disguised traffic attack
The model consists of an 8×8 matrix of switching nodes that deliver packets to computing nodes which are attached to the matrix borders and produce and consume packets. Traffic guns are added to the model to represent traffic attacks. Simulation in CPN Tools revealed simple and dangerous traffic gun configurations. D. A. Zaitsev , T. R. Shmeleva, W. Retschitzegger, B. Pröll Security of grid structures […]
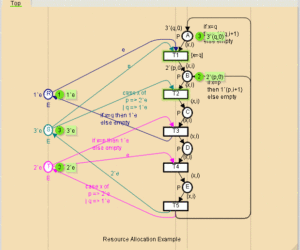
Resource allocation example
This is a small toy example, which is well suited as a first introduction to CP-nets. The CPN model is described in great detail, explaining the basic concepts of CP-nets. Hence, it can be read by people with no/little Petri net background. The CPN model describes how two different kinds of processes are sharing three different kinds of resources. It is simple to understand and […]
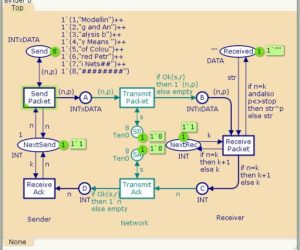
Simple protocol example
This is a small toy example describing a simple protocol by which a sender can transfer a number of packets to a receiver. The communication medium may loose packets and packets may overtake each other. Hence, it may be necessary to retransmit packets and to ignore doublets and packets that are out of order. The example is a modified version of a timed CP-net presented […]
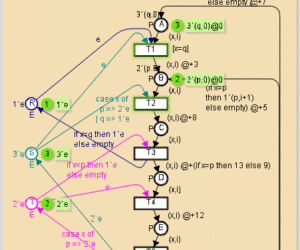
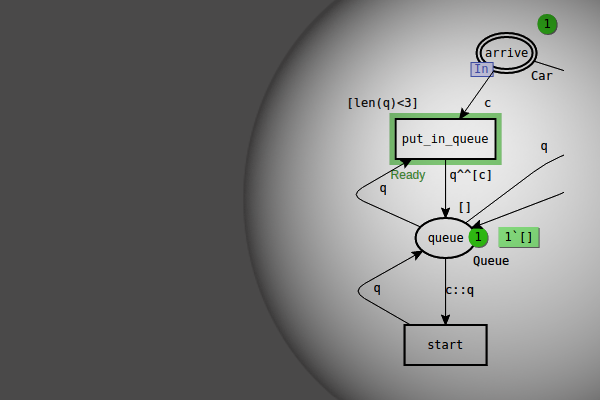
Timed resource allocation example
This is a small toy example which is well-suited as a first introduction to timed CP-nets. It shows how the CP-net from Resource Allocation can be turned into a timed CP-net. The time constructs are described in great detail, explaining the basic concepts of timed CP-nets. The example is taken from Sect. 5.1 of Vol. 2 of K. Jensen. Coloured Petri Nets: Basic Concepts, Analysis […]
Resource allocation example
This is a small toy example which is well-suited as a first introduction to occurrence graphs. The analysis of the occurrence graph is described in great detail, explaining the basic concepts of occurrence graphs. Hence, it can be read by people with no prior knowledge of occurrence graphs. The CPN model describes how two different kinds of processes are sharing three different kinds of resources. […]
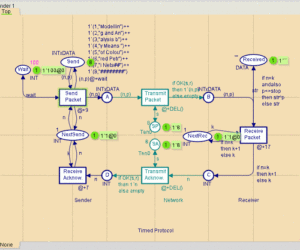
Timed protocol example
This example shows how the CP-net from Simple Protocol can be turned into a timed CP-net. The timed CP-net specifies how long time the individual operations take and how long time the sender should wait before it makes a retransmission. The timed CP-net can be used to experiment with different waiting times to determine which one is the best – in the sense that it […]